What Does A Phishing Email Look Like (Plus 7 Phishing Email Examples)
Phishing scams are on the rise and they’re becoming increasingly sophisticated. But what is a phishing email, why are they so dangerous, and how do you recognize one?
Phishing emails are not new by any means, which is why it is easy to write them off as a threat. However, when you consider that about 83% of organizations were successfully hacked by a phishing email in 2022, it’s become even more important to start phishing awareness training with your employees.
If you’re not sure where to start, keep reading. We are going to break down exactly what to look for, and we’ll show you some common phishing email examples that are being used to steal important company data.
What is a Phishing Email and How Does It Work?
Phishing emails are fake messages sent by attackers to try and steal information from you; information like your passwords and credit card numbers. The reason they work so well is that they are designed to look like real emails you would get from trusted sources, such as banks, popular stores — even coworkers. They often contain links that appear to lead to legitimate websites, but actually take you to malicious sites where you may be asked to enter personal information or click on links that download malware, harmful files or codes onto your computer. When successful, this scheme is used to steal data, money, or personal and company information.
Why Do They Call It ‘Phishing?’
It’s called phishing because hackers are “fishing” for information from a “sea” of users and all hackers have to do is cast their lure hoping for a bite.
Phishing emails are the lure in this analogy. Hackers will set out their bait in the form of these emails and wait for people to click on them and accidentally give up their passwords and other important data.
What Does a Phishing Email Look Like?
Since phishing email attacks are so widespread, it is important for everyone within your organization to know what a phishing email looks like. Here’s what you should look out for:
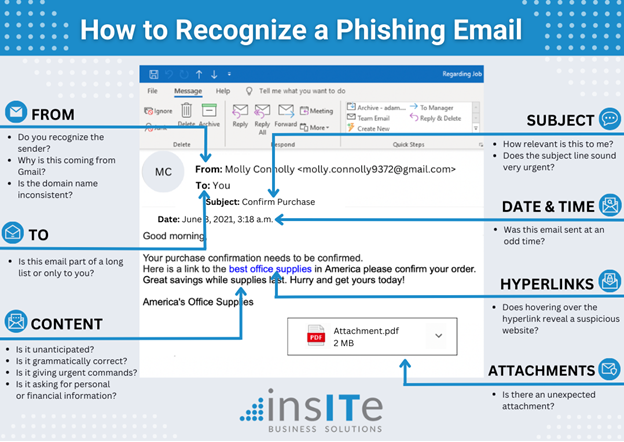
Study the Addresses: Who is it From and Which Email Address is it Sending To?
The sender and recipient email addresses are often the two easiest ways to figure out if you have been sent a phishing email. That’s because hackers like to create email addresses that look like they are from someone you know or the email uses a domain name that looks very familiar. If you are unsure of the email address you are receiving a message from, here are the questions you need to ask:
- Do you recognize the sender?
- Why is this coming from a personal-looking domain like Gmail? (Especially if your organization does not use Gmail)
- Is the domain name inconsistent?
Another area you will want to look into before getting into the email copy will be the “send” section. While phishing emails can be sent out to an individual or to a group of people, a long list of people receiving the same email can be an immediate red flag to a potential phishing scam.
Was the Email Sent at an Odd Time?
Phishing emails can come from anywhere, meaning that the date and time they are sent may not match up with your typical working days or hours. If it was not sent during a normal work schedule, it could signify that the email was sent to “phish” for information.
Pick Apart the Subject Line
Subject lines on phishing emails tend to be very generic and will urge you to take action. This is quite common when companies send sales and marketing emails. If the subject line sounds like “spam” then it probably isn’t worth opening.
Look for subject lines that include words like free, extra income, warning, alert, win, etc. Hackers will use phrases like these to try and get you to log in or purchase something so quickly that you may not even fully read the email or look for some of the red flags we have listed here.
Comb Through the Content
The content in an email can be the most telling and also the most deceptive part of a phishing email.
There can be subtle clues in the content of every phishing email that can show its true purpose, including grammar or unusual requests. Phishing scammers will also try making the email sound urgent to coerce you into taking action. This may be for purchases, using personal login information, or clicking a malicious link.
Another way phishing emails will attempt to trick you is through the use of hyperlinks. Hackers will use hyperlinks to put a link inside the text, hoping you do not see the full URL before clicking on it. When you hover over the hyperlink, does it reveal a suspicious link? If so, make sure it’s from a reputable source.
The last piece of content that phishing hackers will use is adding attachments to their emails. Hackers can use attachments to download malicious software on your computer or server. The advice for potential malicious attachments is simple - if you aren’t expecting an attachment, don’t open it!
The Top 7 Phishing Email Examples
Now that we’ve discussed phishing emails and how to identify them, here are seven of the most common real-world phishing email examples.
1. Fake Invoices
Fake invoices are a popular tool to get an employee to submit a payment, even if they did not purchase the product or service. Organizations can have a multitude of different products they subscribe to and most employees probably do not know what services the company uses and pays for, and which ones they don’t. Hackers will try to use this to their advantage by threatening to shut off the service without immediate payment.
2. Account Deactivation
Account deactivation emails are a popular way to steal a user's login information. A popular phishing account deactivation email is with PayPal. Hackers will send out an email saying your account has been deactivated and to reverse this action, you will need to log in. The website they send you to will look a lot like a PayPal page, and if you submit your login credentials on this site, your PayPal account can be accessed by the hacker.
3. A Message From HR
If you have an HR department, those employees will have access to your personal information, including pay and tax documents. Emails from HR are effective phishing emails because you think they are coming from someone within your organization, and that person is trusted personnel. If you receive an email from HR that contains a suspicious link, always double-check with that department or person first.
4. Fake Google Doc Login
Even if your organization does not use Google Docs, there is a good chance that you have received an invitation to view a document from Google Docs at some point. Hackers will send you a Google Doc request that will look like it is from someone you know with one goal in mind - getting you to use your login credentials to access it.
5. Unusual Activity
As we spoke about phishing scams and the different aspects of an email that you need to question and identify, there is one common goal amongst hackers - creating urgency. Hackers will play on your fear of having your information, accounts, or money stolen by attempting to do those very same things.
These emails will claim the sender noticed “unusual activity” with your account and give you instructions on how to fix it, which will include logging into it. Once you do that, they will have your login information and will be able to access your accounts.
6. Compromised Credit Card
The Comprised Credit Card phishing email works very similarly to the “unusual activity” example. You will receive an email that will look similar to an email from a credit card company you have, and they will ask you to login into your account. This will give the hacker your financial information, and access to your bank accounts.
7. Transfer Funds
Receiving spam emails asking you to transfer funds to someone in another country is one most people are familiar with, but, have you ever received one that is coming from your boss or CEO? This type of phishing email will look like it is from your CEO’s email address and is very urgent, so urgent you will not have time to check in with your CEO about this unusual request. The email content will want you to think you are helping out your company and CEO, but in reality, you are just sending money to an unknown source.
The First Step Toward A More Secure Organization
Phishing emails can be complex and easy to fall victim to without proper training and security protocols. They can target anyone from your CEO to new employees or contractors, which makes them so daunting.
A strategic IT team, like InsITe Business Solutions, can help you test your user susceptibility through training, and help your team continually fight phishing attacks with simulations and testing.
If you are unsure if you are prepared for a phishing email attack, contact us today to figure out where and how you may be vulnerable.
ABOUT INSITE BUSINESS SOLUTIONS:
InsITe helps businesses and manufacturing companies get the most out of current and emerging technologies with a customized IT approach to maximize growth, efficiency, insights, and productivity. InsITe is not a typical IT company selling products for short-term, short-sighted fixes. We invest in long-term solutions for a company’s growth by taking the time to learn its products, process, and business goals before bringing tech into the conversation. In this way, we become much like our Clients’ very own internal IT department with familiar faces who understand the business.
If you have any questions about this post please leave a comment. We read and respond to all comments. Or better yet, give us a call and ask to talk directly to our Founder and CEO Mike Schipper 616-383-9000.
