3 Trending Security Threats Every Manufacturer Needs to Know About
There is no way to sugarcoat it — manufacturing has become the most targeted industry in the world, accounting for nearly a quarter of all cyberattacks. And the aftermath of these cyberattacks can be devastating for businesses, with the average recovery time being one to two weeks after a ransomware attack.
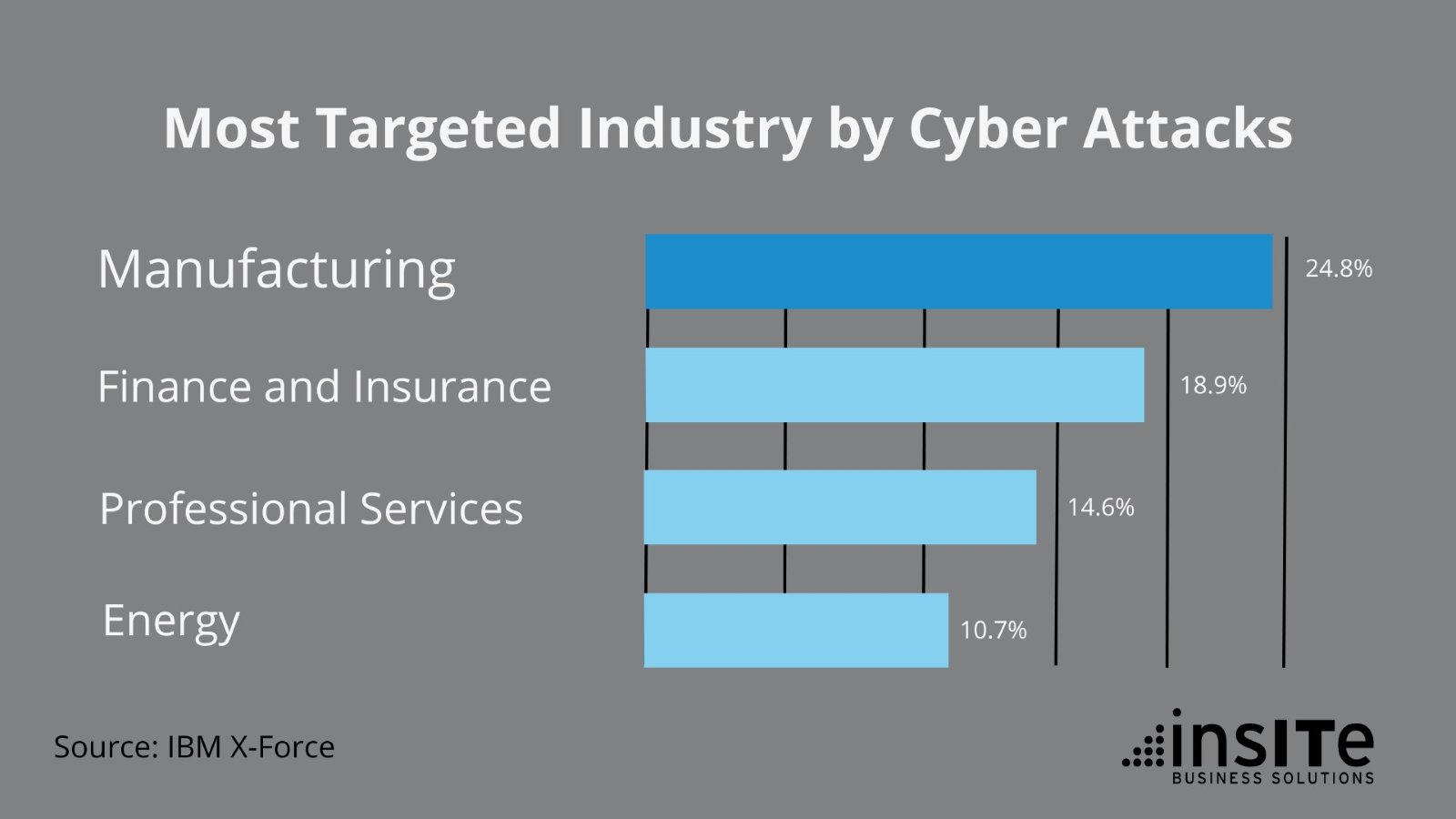
If your company cannot afford to lose a week or two of production then it is vital to learn why manufacturers have become such a huge target, the security threats to look out for, and what you need to know to mitigate these threats.
Why are Manufacturers Being Targeted?
Cyberattacks are increasing in both volume and sophistication, no matter which industry you are in, so why did cyber-attacks in manufacturing increase at such an alarming rate?
There are a variety of reasons why the target on the manufacturer’s back is only getting bigger:
- Any disruption to the supply chain can have a major ripple effect and any cyberattack on a single supplier, manufacturer, or fabricator can negatively impact the whole chain. And cybercriminals know this. This devastating potential puts huge pressure on the manufacturer to pay a ransom to a cybercriminal to keep production going.
- Manufacturers across the industry also have a unique issue with technology, where they have machinery connected to their network that is 10-20+ years old when having extra cybersecurity was just an afterthought. This has left many devices on shop floors lacking in security, leaving them vulnerable to cyberattacks.
- IT directors and teams routinely have more work than they can handle. Thinking of the IT professionals at your company, it is common to see them overwhelmed and spread thin with their current workload, constantly having to put out fires on top of being responsible for a full technology plan. If they are forced to respond to every issue, then they do not have much time to work on proactive cybersecurity, which can add to your company’s vulnerabilities.
Trending Security Threats That Need to be on Your Radar
Keeping up with trending security threats can be difficult, especially if your IT team is already spread thin, but as cybercrimes become more frequent and sophisticated, it is essential to do it, so you have the right security strategy in place to protect your business. Here are some of the top security threats that are impacting manufacturers right now:
1. Ransomware and RaaS
Ransomware has plagued the industry for years. Ransomware is a type of malware that cybercriminals will use to get into your system, steal your data, and demand a ransom for its return. As we mentioned earlier, ransomware is commonly used against manufacturers because cybercriminals know that most manufacturers cannot afford to delay production, making them more likely to pay the ransom to avoid downtime.
Cybercrime is no longer just someone sitting in their basement — it has evolved into its own industry. Ransomware has become such a prevalent threat that it has even evolved into its own business, called Ransomware as a Service (RaaS). Hackers are creating groups that are designed to attack businesses and collect ransoms, meaning these attacks can come from anyone. This is why it is critical to invest in cybersecurity and know where you may be vulnerable.
2. Increasing Number of Connected Devices (IoT)
The manufacturing industry has embraced Industry 4.0 and IoT as it has helped improve productivity and efficiency with increased visibility into the data coming from your shop floor. But as more devices are connected to your network, cybercriminals have more devices they can target. This means that one vulnerable device can lead to the disruption of an entire network.
When manufacturers have older equipment, this can also present a unique issue with their technology. Cybersecurity was an afterthought for machinery that is over 10 years old, and now that this equipment is connected to your network, it can be vulnerable to cyberattacks.
3. Phishing
Phishing email scams are one of the most recognizable cyberattacks, where hackers will send fake messages posing as a trustworthy source with the goal of stealing information from you. When you receive one that is done poorly you may think to yourself “How could anyone fall for this?” But phishing emails are increasing in volume to the point where 83% of organizations were successfully hacked by a phishing email last year. Phishing emails cannot be overlooked and can be easy to fall victim to without employee training and security protocols.
How do You Mitigate these Security Threats?
When talking with businesses about cybersecurity, many have the same response — “What’s the worst that could happen?” Well, in many cases, it could be the thing that puts you out of business. As these cyberattacks continue to evolve, it has never been more necessary to invest in your security strategy.
Creating a security strategy is no simple task, but there are resources that can help you get started, including our IT Security Checklist. If you are not ready to go fully into a security checklist, another good place to start is by creating an inventory of all your connected devices. Once you have this, ask yourself “Do I feel confident in my security for each of these devices?”
If the answer is no, then it is time to create a plan to protect each one of your devices, including vulnerability assessments, backup and recovery plans, and cybersecurity training for your employees.
It is important to note that simply checking an item off the security checklist does not end the process. Having a layered approach that includes having usable backups and ensures your operating systems stay current and up to date will help to protect your entire network.
Managed Service Providers (MSPs) can be helpful when implementing your security strategy, but not every MSP works the same way. It is crucial that your MSP has a security-first mindset and will take a strategic approach to your plan. Your IT infrastructure is complex, so you need to make sure that you are not getting a cookie-cutter approach to your cybersecurity.
ABOUT INSITE BUSINESS SOLUTIONS:
InsITe helps businesses and manufacturing companies get the most out of current and emerging technologies with a customized IT approach to maximize growth, efficiency, insights, and productivity. InsITe is not a typical IT company selling products for short-term, short-sighted fixes. We invest in long-term solutions for a company’s growth by taking the time to learn its products, process, and business goals before bringing tech into the conversation. In this way, we become much like our Clients’ very own internal IT department with familiar faces who understand the business.
If you have any questions about this post please leave a comment. We read and respond to all comments. Or better yet, give us a call and ask to talk directly to our Founder and CEO Mike Schipper 616-383-9000.
